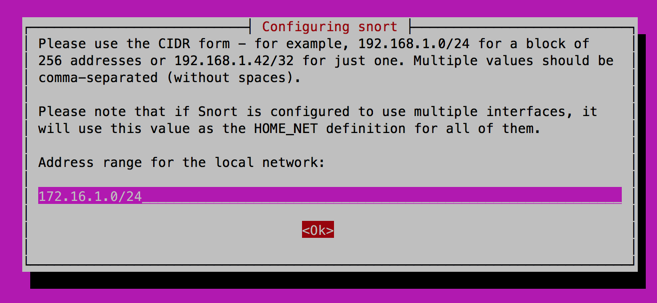
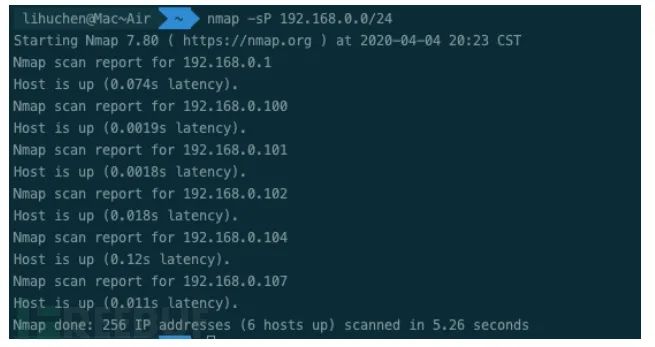
Nmap And Snort. Ping Scan [-sP] This scan type lists the hosts within the specified range that responded to a ping. Nmap ("Network Mapper") is a free and open source utility for network exploration and security auditing. Snort scans the signature of this attempt to determine if it is different from the allowed network scanning tools (such as NMAP), and is therefore likely an attack. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Therefore be smart and add a rule in snort which will analyst. In this video, we are testing Snort against NMAP various scan, which will help you as network security analyst to set up snort rule in such a way so that the. One of my highest Nmap development priorities has always been performance. Claim Nmap and update features and information.
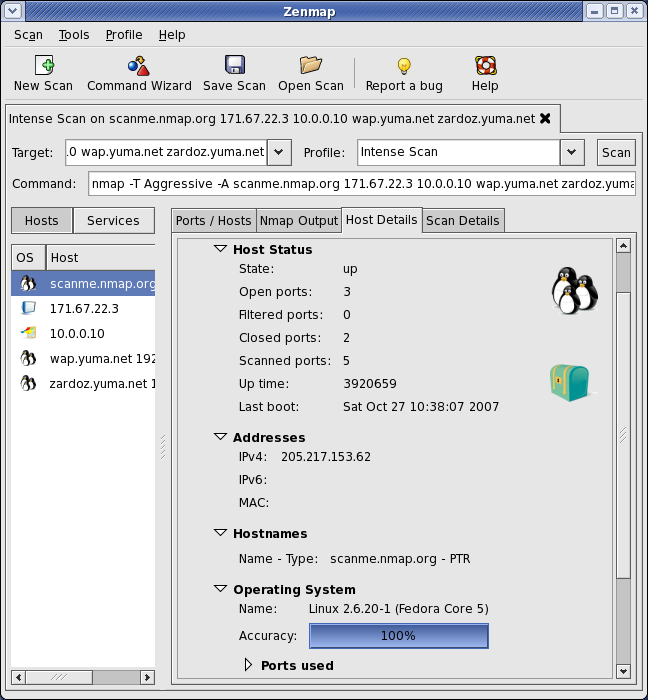
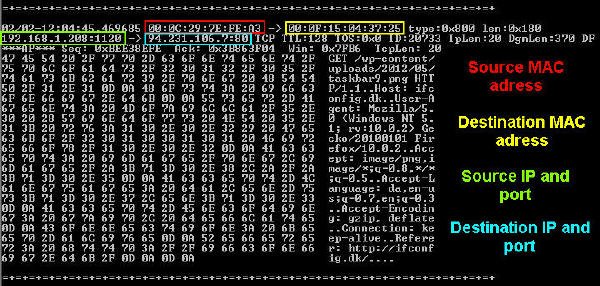
Nmap And Snort. This option allows Snort to alert on several types of stealth scans, such as those used by Nmap, to try to hide from other detection tools. Alert Message INDICATOR-SCAN synscan portscan Rule Explanation A host has scanned the network looking for vulnerable servers. Snort scans the signature of this attempt to determine if it is different from the allowed network scanning tools (such as NMAP), and is therefore likely an attack. Nmap View Product Snort Snort Rule Structure Snort's intrusion detection and prevention system relies on the presence of Snort rules to protect networks, and those rules consist of two main sections: The rule header defines the action to take upon any matching traffic, as well as the protocols, network addresses, port numbers, and direction of traffic that the rule. As we know any attacker will start attack by identifying host status by sending ICMP packet using ping scan. Nmap And Snort.
Nmap ("Network Mapper") is a free and open source utility for network exploration and security auditing.
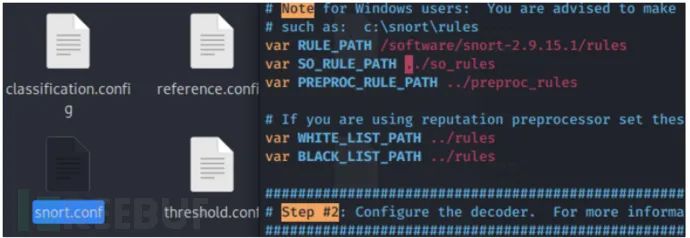
Snort – Individual SID documentation for Snort rules.
Nmap And Snort. Snort can be downloaded and configured for personal and business use alike. Snort scans the signature of this attempt to determine if it is different from the allowed network scanning tools (such as NMAP), and is therefore likely an attack. This option allows Snort to alert on several types of stealth scans, such as those used by Nmap, to try to hide from other detection tools. It can be configured to simply log detected network events to both log and block them. It allows you to detect which computers are online, rather.
Nmap And Snort.