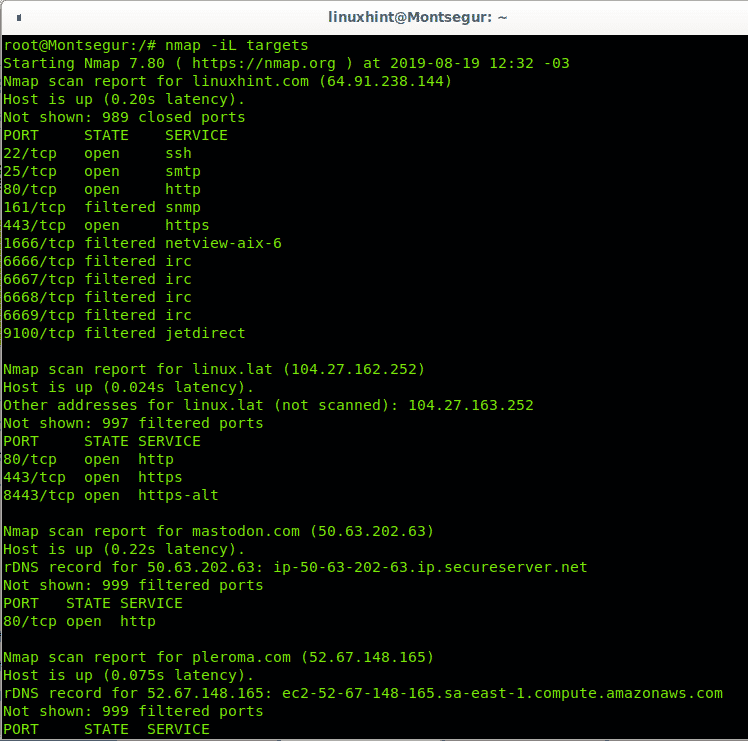
Nmap Force Scan. Port scanning methods supported by Nmap. the section called "TCP SYN (Stealth) Scan ( -sS )" (-sS) Nmap Network Scanning. UDP Scan ( -sU) While most popular services on the Internet run over the TCP protocol, UDP services are widely deployed. One of the very first steps in any network reconnaissance mission is to reduce a (sometimes huge) set of IP ranges into a list of active or interesting hosts. How to use Nmap to scan for open ports. You can pass in the -p- flag as specified in the nmap help page. Nmap, which stands for "Network Mapper," is an open source tool that lets you perform scans on local and remote networks. Say goodbye to the hassle of trying to remember the exact syntax for your Nmap commands! Another option would be to pass in the explicit range you want with the -p flag.
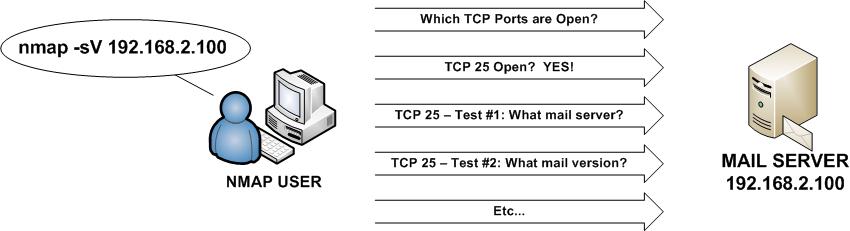
Nmap Force Scan. While NSE has a complex implementation for efficiency, it is strikingly easy to use. I am often on one computer in my house and I would like to SSH to another one, but often don't know the IP address of the one I want to connect to. At its most basic, Nmap can scan a single port by just specifying the target port number with the -p option. One of the very first steps in any network reconnaissance mission is to reduce a (sometimes huge) set of IP ranges into a list of active or interesting hosts. This will force Nmap to perform a TCP scan of scanme.nmap.org using the interface <INTERFACE>. Nmap Force Scan.
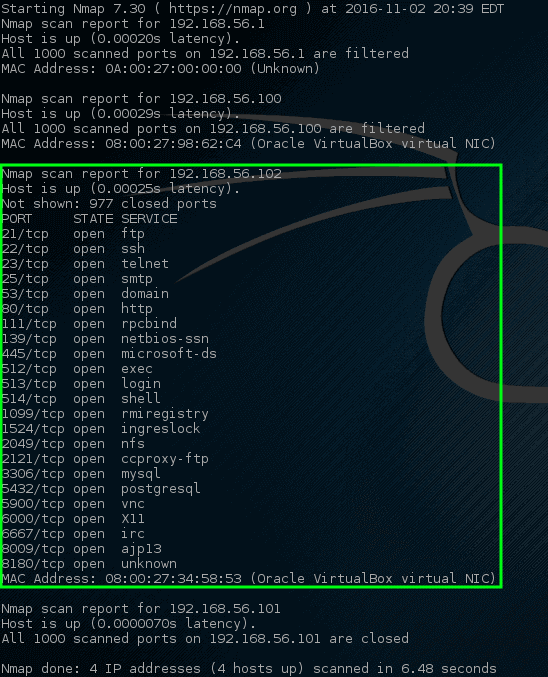
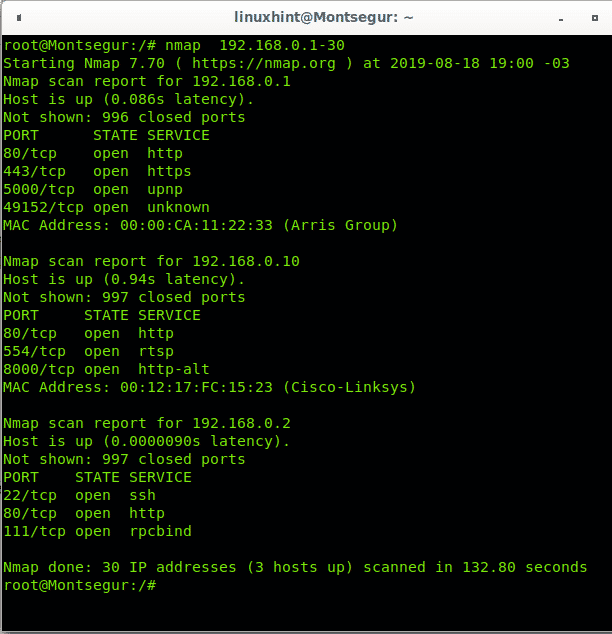
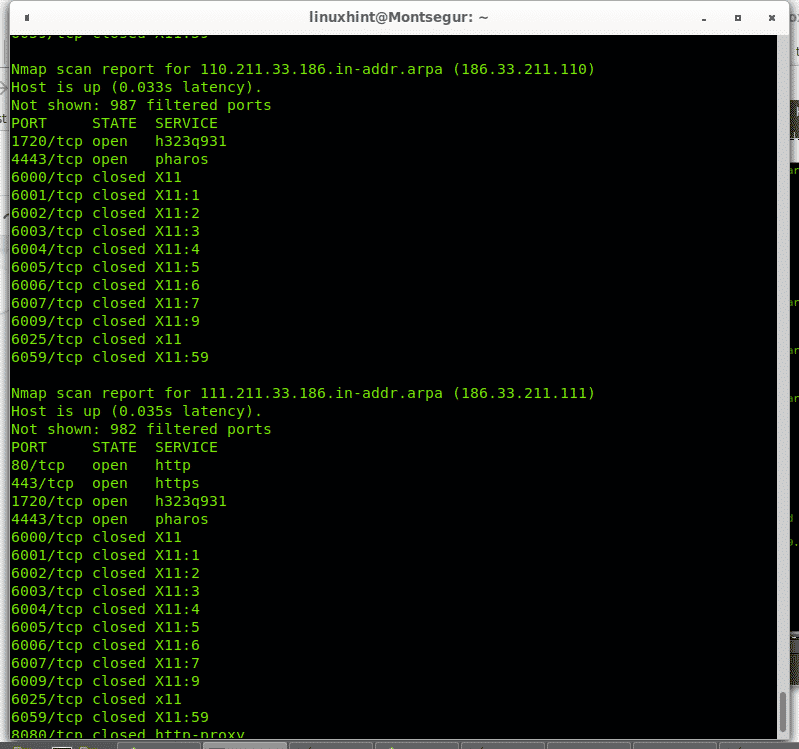
Nmap Command to Scan for Open Ports.
Nmap, which stands for "Network Mapper," is an open source tool that lets you perform scans on local and remote networks.
Nmap Force Scan. At its most basic, Nmap can scan a single port by just specifying the target port number with the -p option. Nmap allows network admins to find which devices are running on their network, discover open ports and services, and detect vulnerabilities. One of the very first steps in any network reconnaissance mission is to reduce a (sometimes huge) set of IP ranges into a list of active or interesting hosts. This is the basic format for Nmap, and it will return information about the ports on that system. While NSE has a complex implementation for efficiency, it is strikingly easy to use.
Nmap Force Scan.